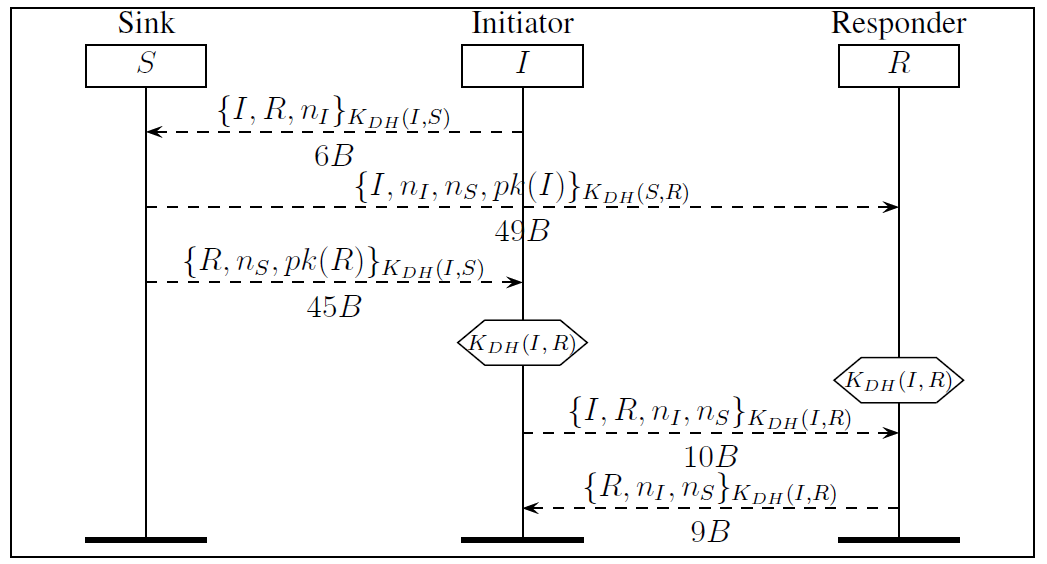
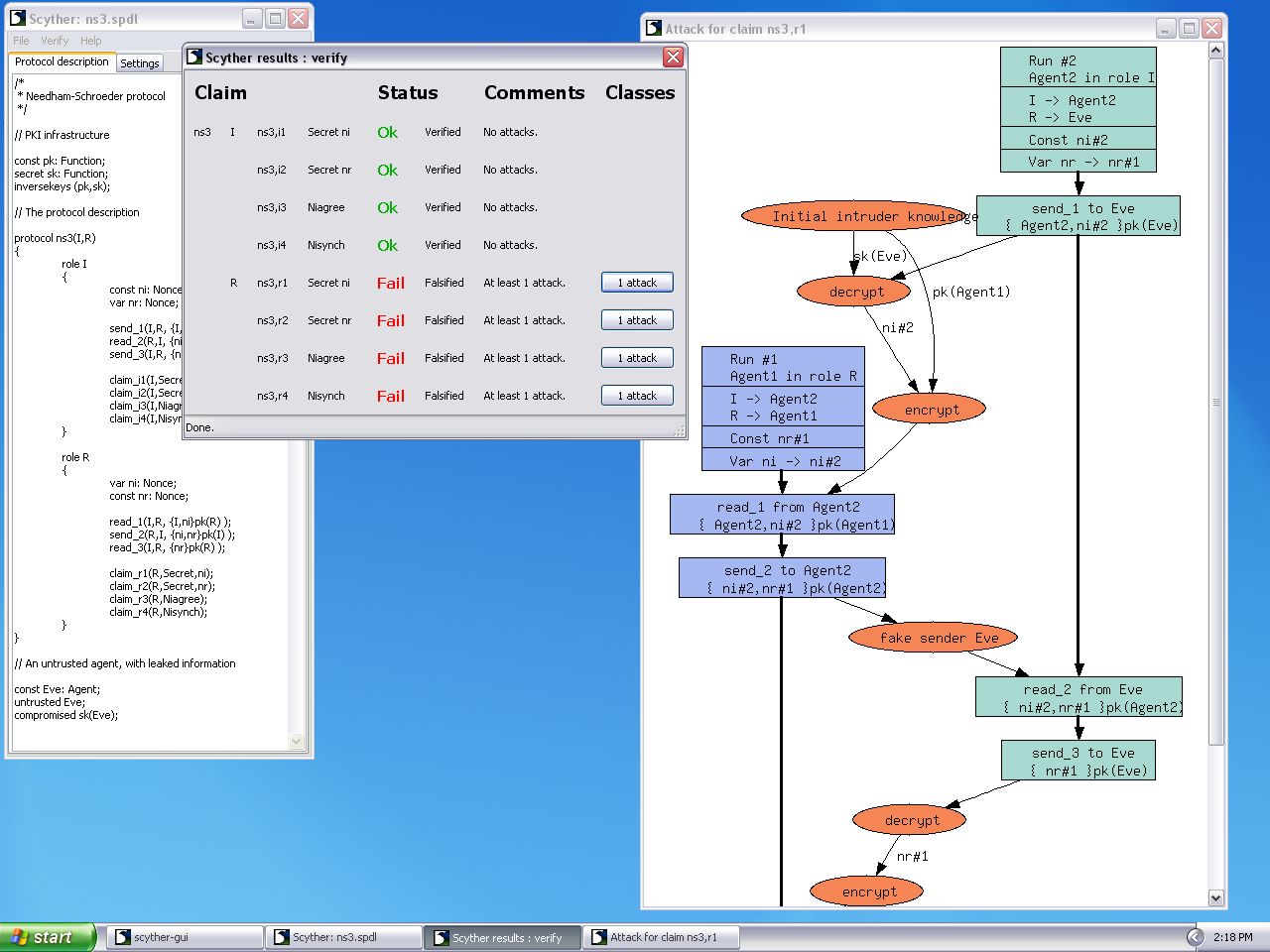
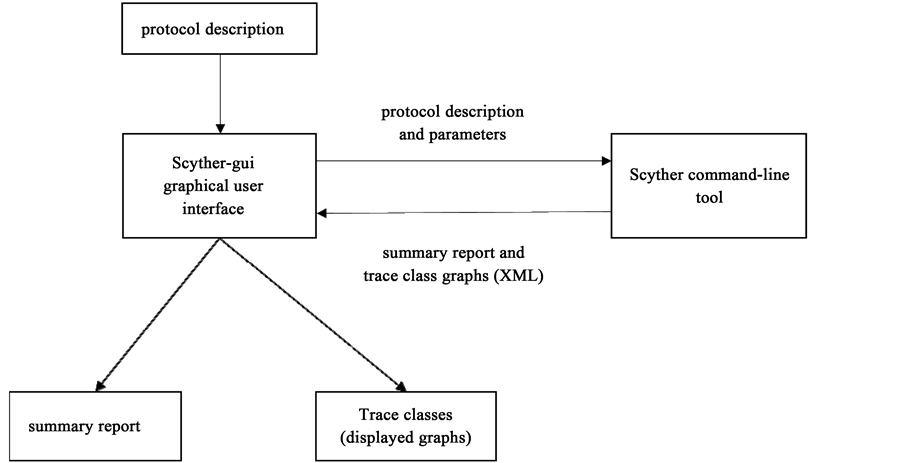
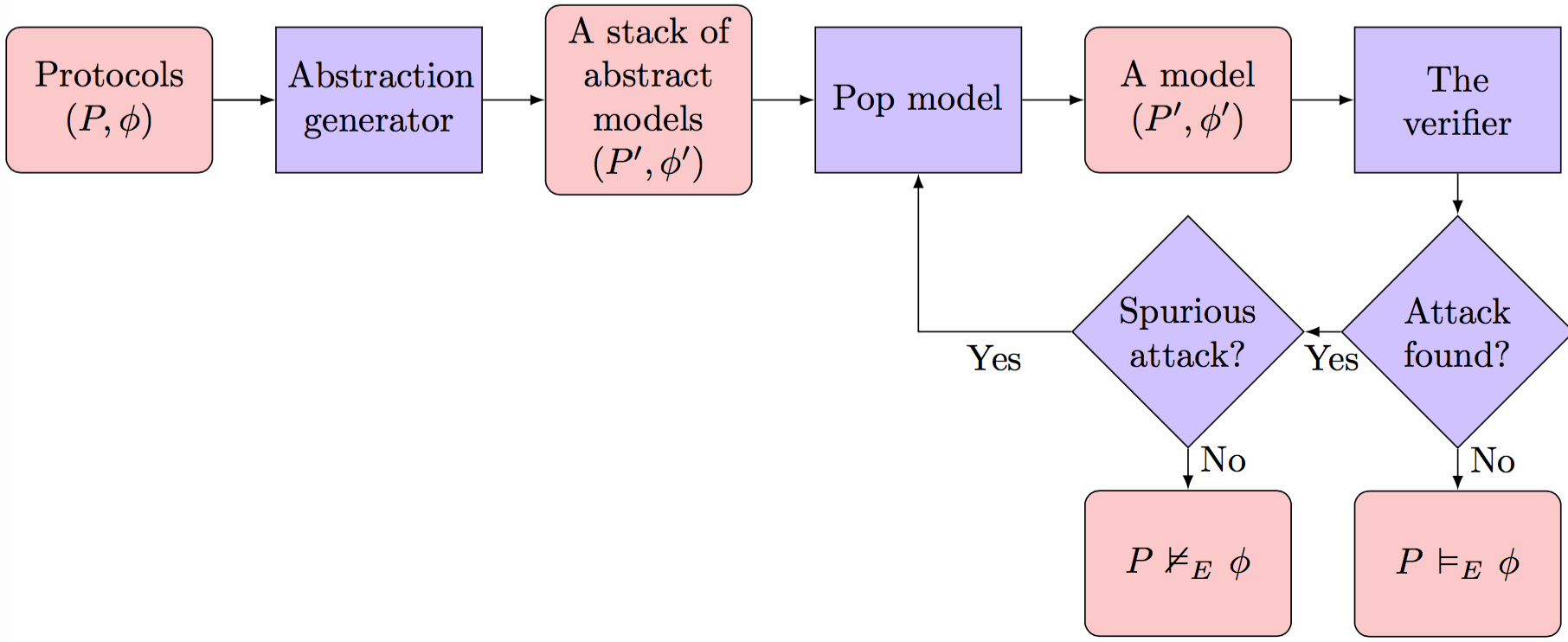
Assessment of Threats to the Security of the Cryptographic Authentication Mechanisms of the Monitor Devices of Vehicles | KnE Engineering

Scyther (Formal Verification Tool) Installation on Windows #Scyther #Formalverification #Windows - YouTube

Result using 'automatic claim' procedure in Scyther tool (see online... | Download Scientific Diagram
![PDF] Analysis and Verification of a Key Agreement Protocol over Cloud Computing Using Scyther Tool | Semantic Scholar PDF] Analysis and Verification of a Key Agreement Protocol over Cloud Computing Using Scyther Tool | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/df932f9db948e0e49c26a748ca2eec9d76e3c118/6-Figure4-1.png)
PDF] Analysis and Verification of a Key Agreement Protocol over Cloud Computing Using Scyther Tool | Semantic Scholar
Snapshot of SCYTHER tool: experimenting using various types of attacks | Download Scientific Diagram

scyther tool installation on windows. Scyther model checker installation on windows OS. Formal Verif - YouTube

Cryptanalysis and improvement of the YAK protocol with formal security proof and security verification via Scyther - Mohammad - 2020 - International Journal of Communication Systems - Wiley Online Library

The results using 'verification claim' procedure in Scyther tool (see... | Download Scientific Diagram